Application-Layer DDoS: New Weapon of Choice
The sheer variety of online threats today in the cyber landscape can be mind-boggling. This article will address one of the more pressing issues for online businesses–Application Layer DDoS—what it is, and how to protect against it.
“Low and Slow”
As opposed to large-scale, flashy volumetric attacks, Application Layer Distributed Denial of Service (DDoS) works in more subtle ways to disrupt websites. Instead of overwhelming a target network with floods of information, Application Layer DDoS attacks are smaller and spread over many connections.
Hackers start by setting up several TCP connections with a target server. This way, the target sees the bot-generated requests as ‘legitimate,’ making them even more difficult to detect. In fact, many Application Layer DDoS are executed without the victims even realizing they are getting hit. They may write off the disruption as a connectivity issue. Businesses may believe they are protected by their traditional security measures like firewall or load balancers, but these are ineffective against ‘legitimate’ requests.
As the name suggests, these attacks aim at applications, like HTTP, by taxing a server’s memory resources. Then the attack may move on to other applications, slowly bringing down the site piece by piece. Clearly, security in these cases requires more than just a big network.
DDoS in the Field
Back in October, Incapsula, a leading security firm, had a drawn out battle against one of the most sophisticated DDoS attacks of all time. It began shortly after one of the target company’s partners left on bad terms, leading the firm to believe he was at the bottom of the attack.
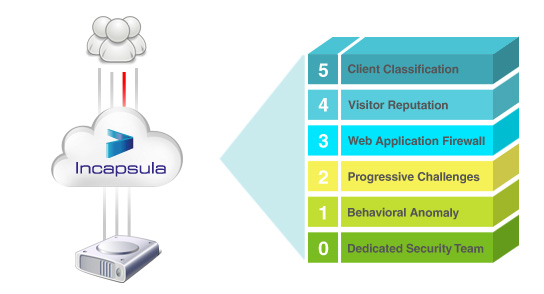
The first tremor came from a short-lived SYN flood, a relatively simple threat to handle. Next came a head-on HTTP flood at a heavy 10M requests/second. This alone would be enough to take down most servers, but it could not trick Incapsula’s Client Classification system.
But then the hackers got serious. They began hitting other applications like AJAX, and even Incapsula itself. They came with bots able to capture session cookies, bots with human-like user-agent, and bots with human behavior. Incapsula countered with CAPTCHA challenges. On and on the attack rained down, for over 7 weeks. Fortunately the target was prepared with 3rd party security, but most companies do not have the wherewithal to arm themselves with proper defenses.
Another potentially devastating Application Layer DDoS attack came in November. This threat used PhantomJS bots to mimic human operations. These bots could retain cookies as well as run JavaScript. But because of the spike in requests, and the diversity of IP locations, the target’s security firm determined this behavior to be malicious.
These deviant hackers constantly changed IPs, making it useless to simply block a bad IP and move on. At the height of the attack, the bots were generating over 690 million requests a day. Not too shabby, but not enough power or intricacy to bring down high-level security services.
The Power in Your Hands
You can defend yourself from Application Layer DDoS with knowledge. For example, white hat hackers recently published a guide for counter-attacking DDoS troublemakers who use the popular Dirt Jumper hacking tool kit. For those who do not have the time to spread their energy should consider hiring a 3rd party security firm. The top cyber protection agencies offer a range of security options to fit your businesses unique needs. Keeping fighting the good fight.